How to Configure and Run Scans Using The API Written on . Posted in How-To.

Update September 27, 2025: This API guide is now deprecated. If you would like to learn more about integrating with the Panoptic Scans API, please click here.
Once you're registered, configuring vulnerability scans with the Panoptic Scans API is easy. First, log in and click on your user icon in the upper right corner of the page. Here, you can find settings.
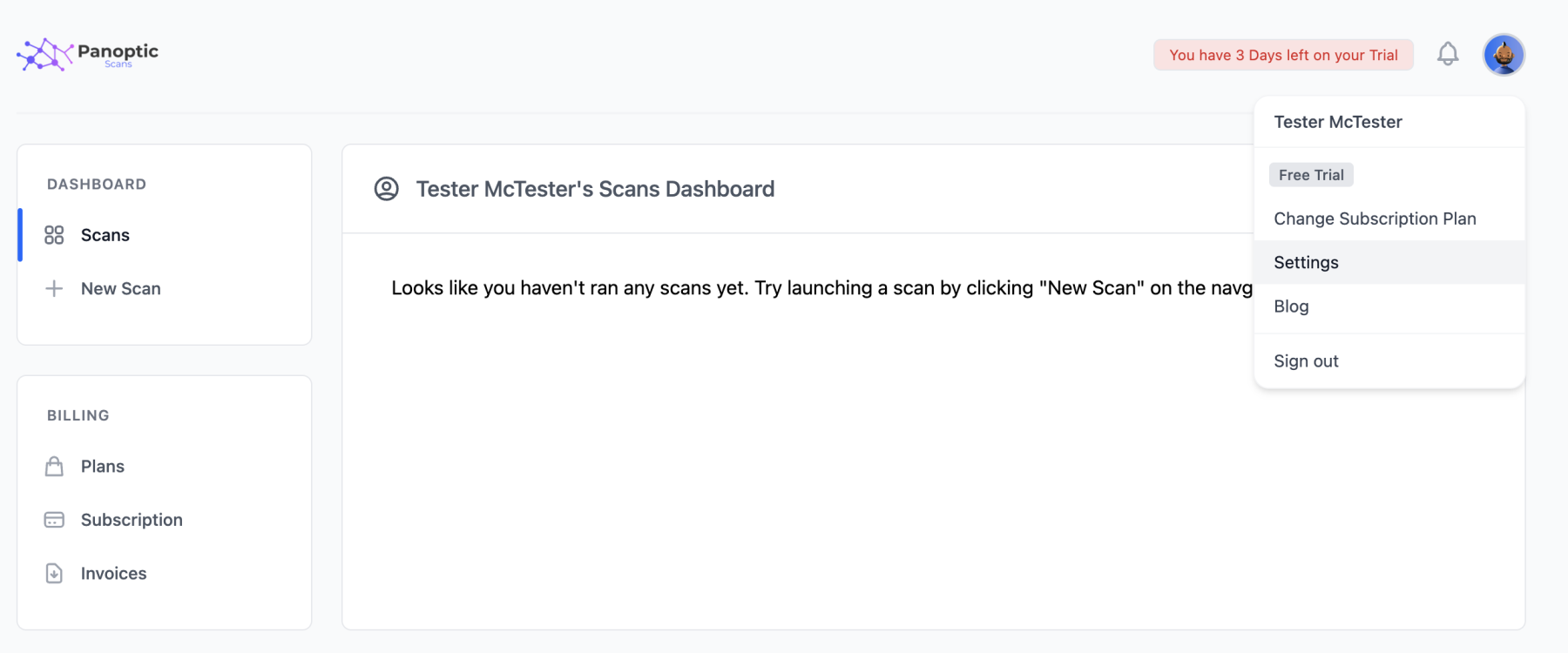
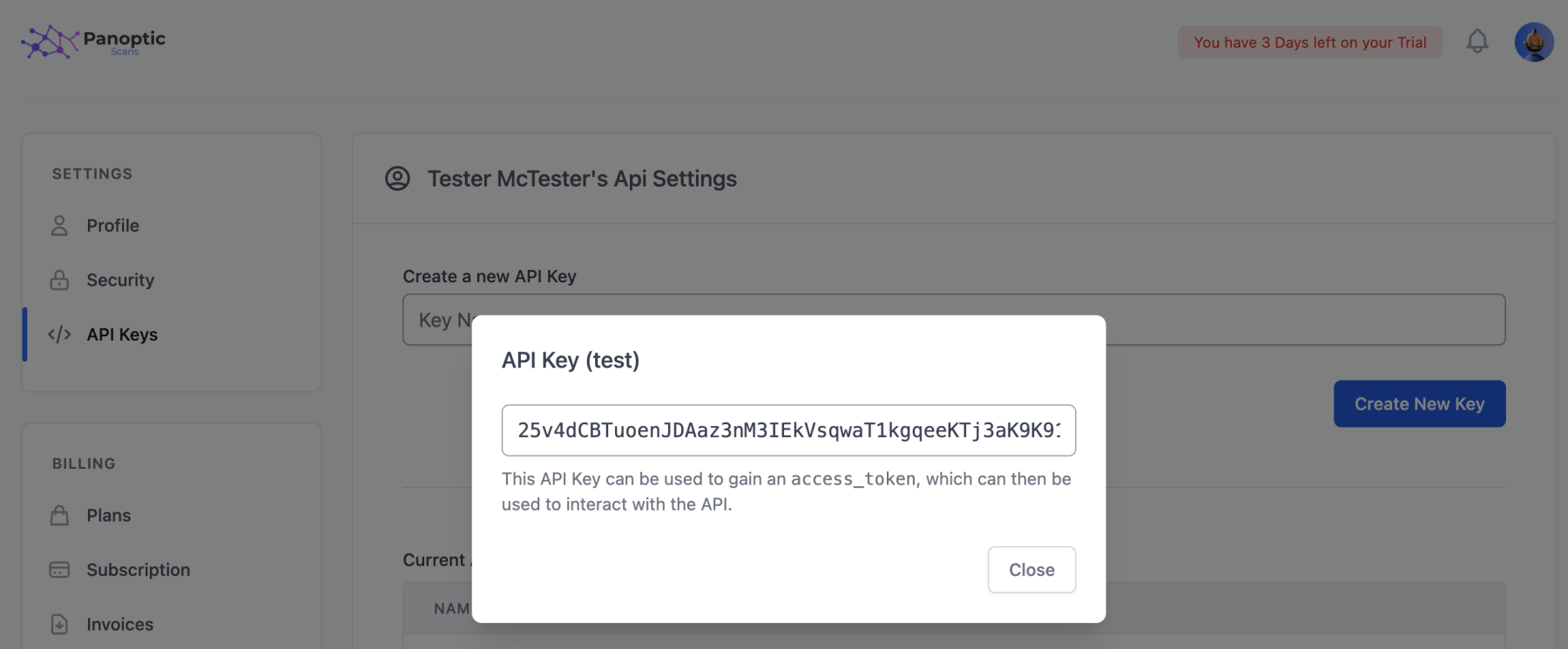
Next, click on API Keys in the left navigation bar and enter the name for your API key. Once you've clicked on "Create New Key" you can view your key.
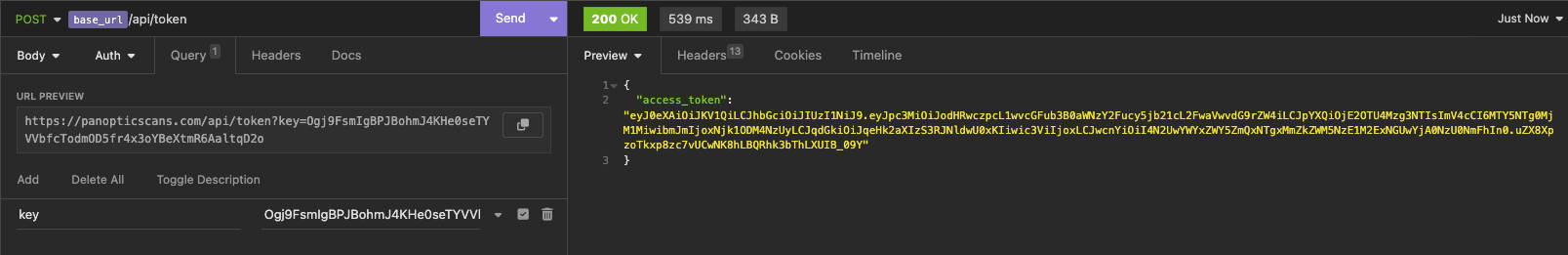
Using this key, you will send a POST request to the /api/token route and specify the key as a URL variable. This request will result in a reponse with an access token to be used for additional interaction with the API.
Set the Authorization request header to hold the access token. Now, we request all scan results.
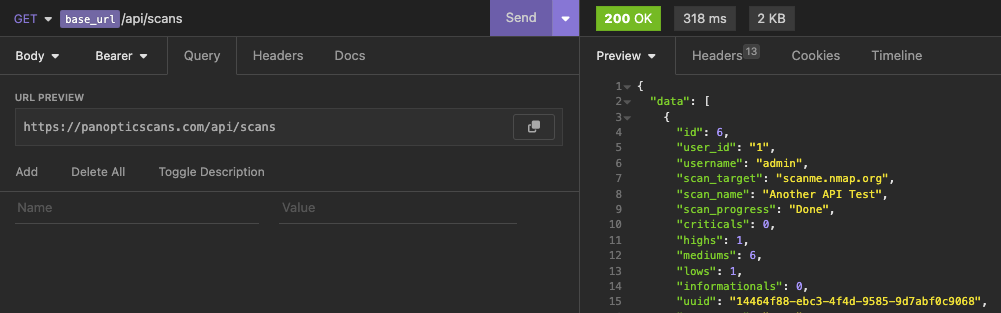
The API also enable you to configure new scans by specifying the requisite details. Once a new scan is configured, it's unique identifier is returned.
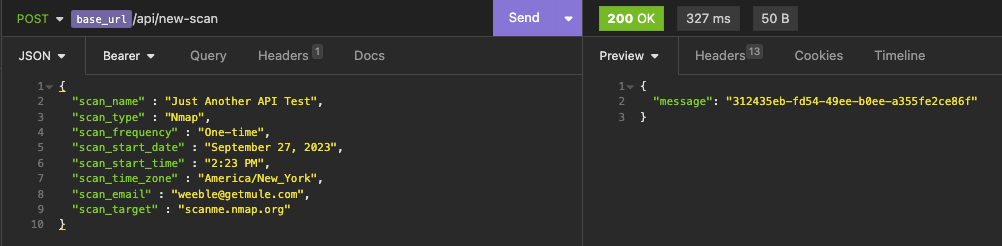
This unique identifier can then be used to retrieve the scan results.
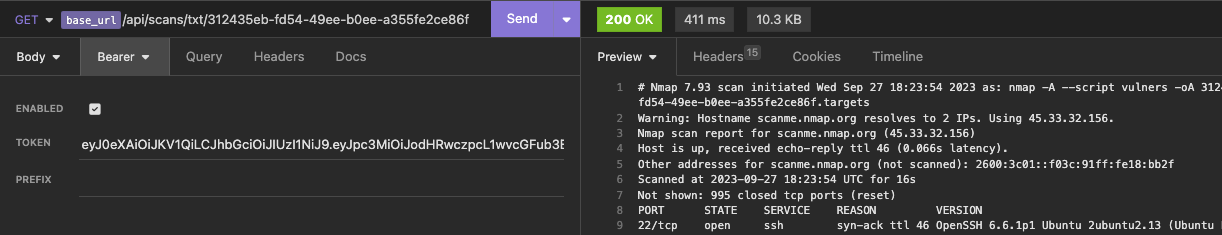
Scan names can also be changed via the API.
And scans can be deleted via the API.
The full Panoptic Scans API Insomnia collection can be downloaded here.