Hosted Nuclei Vulnerability Scans with Panoptic Scans Written on . Posted in How-To.

Streamline Your SOC 2 Compliance with Hosted Nuclei Scans
If you're a SaaS leader, the term "SOC 2" probably comes up a lot. It's the gold standard for security, a key that unlocks enterprise deals and builds customer trust. But preparing for an audit can feel like a monumental task, especially when it comes to proving you have a handle on vulnerabilities.
Your auditor will ask: "How do you identify and manage vulnerabilities?" A strong answer here is critical. While SOC 2 doesn't mandate a specific tool, it requires a robust process for detecting new threats, and that's where vulnerability scanning becomes your best friend. This is where the powerful open-source scanner, Nuclei, shines. But who has time to manage another tool?
That's one of the reasons we built Panoptic Scans: to give you the power of Nuclei, fully hosted and automated, so you can focus on your business while we help you ace your audit.
What is Nuclei, and Why Should You Care?
Think of Nuclei as a highly efficient detective for your applications and infrastructure. It uses a massive, constantly updated library of "templates" to check for thousands of known vulnerabilities, misconfigurations, and security flaws. It's fast, thorough, and trusted by security teams worldwide. For a SaaS business, this means you're getting cutting-edge checks against the very threats that could impact your customers' data.
Your Quick Path to SOC 2-Ready Scanning
We believe proving compliance shouldn't be complicated. Here's how you can set up an automated, audit-ready scanning program in just a few minutes, no engineers required.
Step 1: Tell Us What to Protect
First, define the assets you need to scan for your SOC 2 audit. This could be your main web application, APIs, or other internet-facing infrastructure.
- Log in to your Panoptic Scans dashboard.
- Navigate to the "Targets" section.
- Click "Add Target" set the scan type to Nuclei, and enter the domain or IP address. It's that simple.
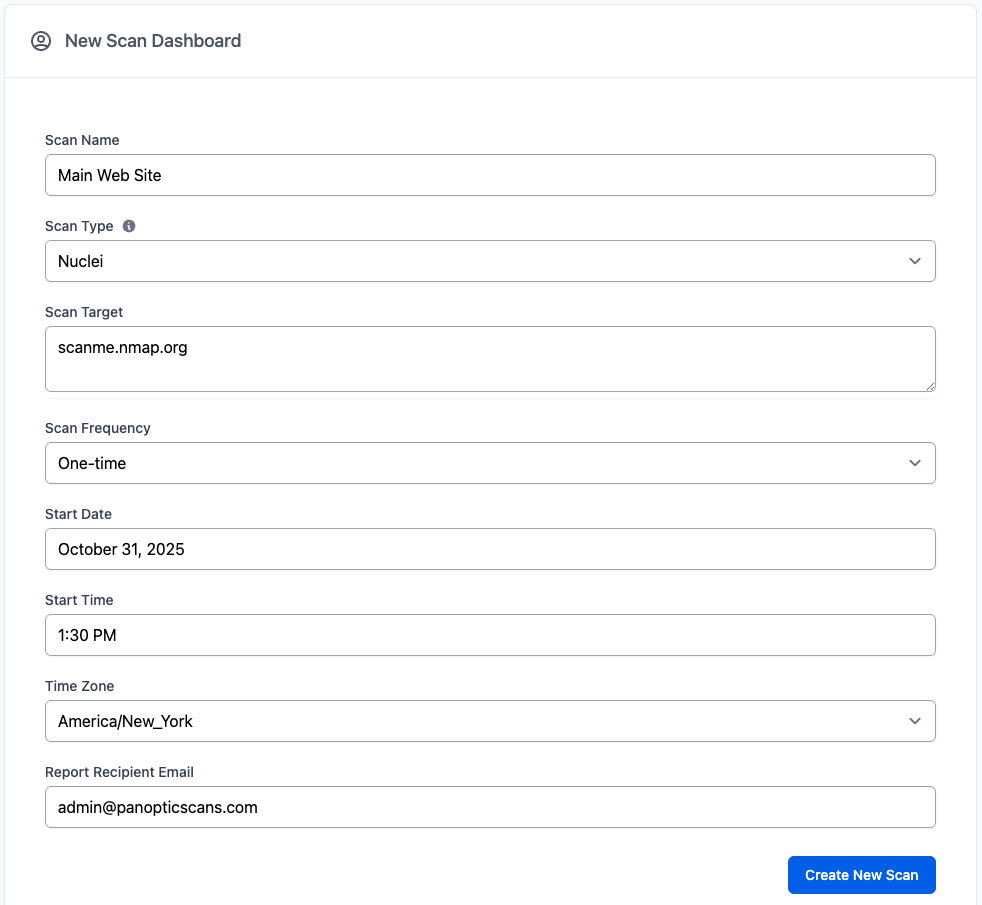
Adding your key application as a target takes seconds.
Step 2: Set It and Forget It
Continuous monitoring is a cornerstone of SOC 2. Your auditor wants to see a consistent, ongoing process. With Panoptic Scans, you can schedule your Nuclei scans to run automatically.
- Go to the "Scans" section and click on the Edit Scan button in the Actions column.
- Check your target and choose the "Nuclei Vulnerability Scanner."
- Set a recurring schedule, we recommend weekly to start. This demonstrates a proactive security posture to your auditor.
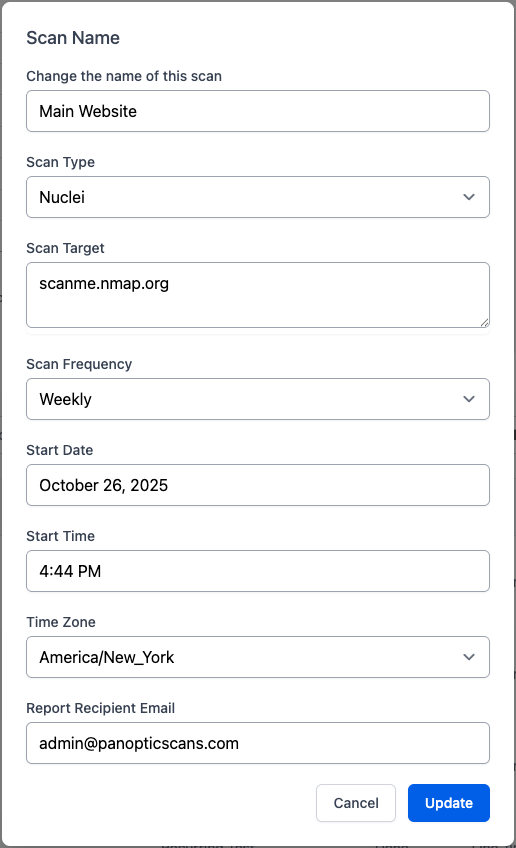
Schedule weekly or monthly Nuclei scans to ensure continuous compliance.
Step 3: Let Us Handle the Rest
Click "Launch Scan," and you're done. Panoptic Scans manages the entire process—no servers to maintain, no software to update. We run the scans, and you get the clear, actionable results you need for your SOC 2 evidence.
From Scan to Audit-Ready Evidence
When the scan is finished, we don't just hand you a list of technical jargon. We provide clear results that you can act on and show to your auditor.
The 10,000-Foot View
Your Vulnerabilities Dashboard immediately shows you what matters most, with vulnerabilities automatically prioritized by severity. This helps you prove to your auditor that you have a process for identifying and triaging risk.
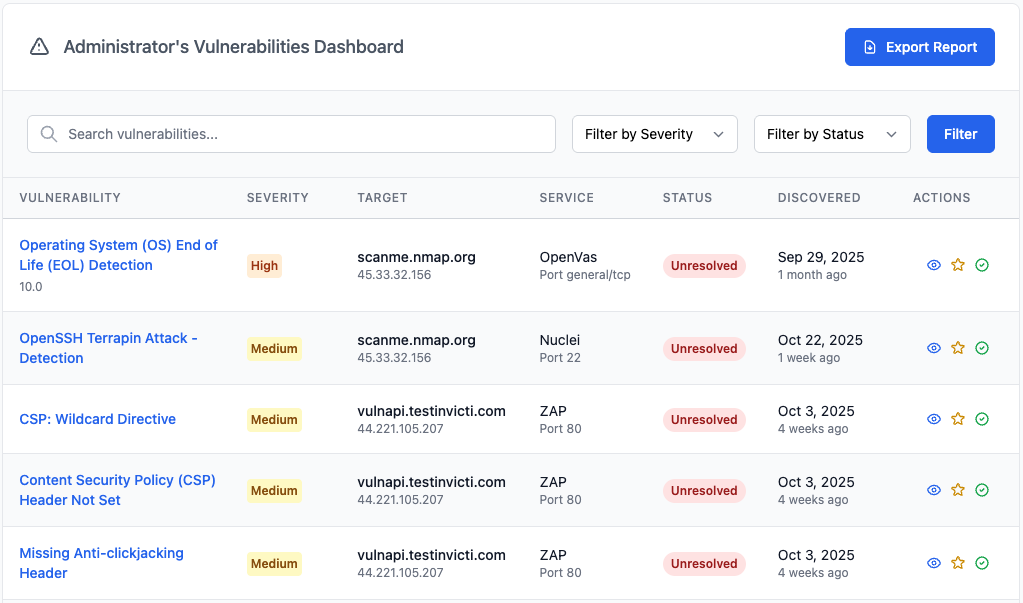
The dashboard gives you an instant, risk-based overview for easy reporting.
Details When You Need Them
For each vulnerability, you can drill down to see which assets are affected and get straightforward advice on how to fix it. This is your evidence of a robust vulnerability management program in action.
- What's the problem? A clear description of the vulnerability.
- How serious is it? A severity rating to guide your focus.
- Where is it? A list of every affected system.
- How do we fix it? Actionable guidance for your team.
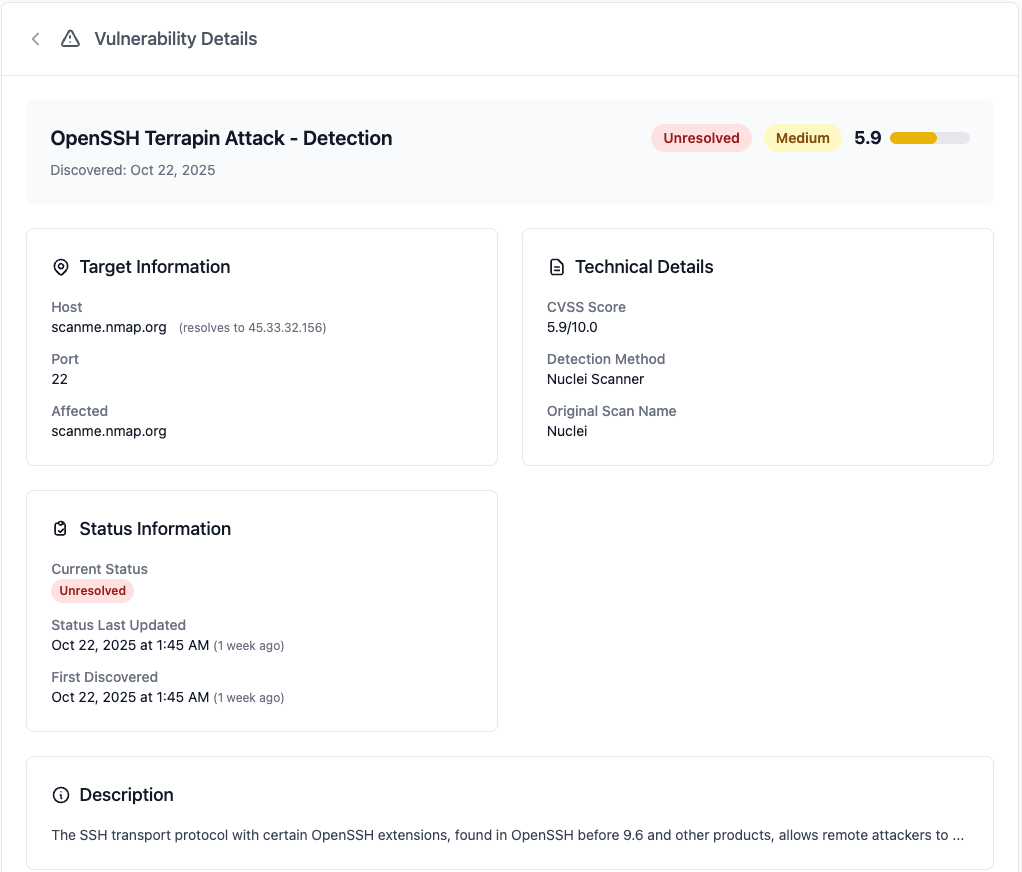
Easily export vulnerability details to share with your team or your auditor.
The Business Case for Hosted Nuclei Scans
Using Panoptic Scans isn't just about checking a box for SOC 2. It's a strategic decision that delivers real business value.
- Accelerate Your SOC 2 Audit: Walk into your audit with a complete record of continuous vulnerability scanning and remediation efforts.
- Reduce Engineering Overhead: Free up your technical team from managing security tools so they can focus on building your product.
- Build Customer Trust: Proactively securing your platform is one of the strongest signals of trust you can send to your customers.
- Continuous Compliance, Not Just a Checkbox: Move from painful, once-a-year audit prep to a state of continuous, automated security.
Pass Your Next Audit with Confidence
Don't let vulnerability management be a roadblock in your SOC 2 journey. With Panoptic Scans, you can implement a best-in-class Nuclei scanning program that strengthens your security, builds trust, and provides the evidence you need to sail through your audit.
Ready to simplify your SOC 2 compliance? Sign up for Panoptic Scans today and get your first scan running in minutes.